
3 Cyber Threats Every C-level Leader Should to Be Aware of
Discover three lesser-known, but equally threatening items posing risks to the health of your…
As security threats increase, they are also becoming more sophisticated and targeted. Are you confident that your current security measures are sufficient?
When it comes to protecting your company, this isn’t worth gambling on. In our experience, even the most impressive IT teams have blind spots, so it helps to have a set of security standards to minimize vulnerabilities.
That’s why companies often rely on CIS benchmarks, employing the CIS recommendations to raise their security up to a reasonable standard. If your company handles sensitive data like financials or healthcare information, you’ll want to keep reading.
“CIS benchmarks” refer to the Center for Internet Security benchmarks. These benchmarks are a set of best practices and guidelines for securing various computer systems and networks. They are developed by the Center for Internet Security, a nonprofit organization that focuses on improving the cybersecurity posture of organizations and individuals.
The benchmarks are intended to help organizations improve their security and prepare for cyber threats by following industry-recognized standards.
By implementing these benchmarks across all types of IT systems, you create a more secure IT environment that can be further strengthened with specific security solutions. These are tried-and-true best practices, and CIS provides the instructions you need to help you understand potential vulnerabilities and solutions to fix them.
CIS benchmarks provide detailed recommendations for securing operating systems, software applications, cloud environments, and network devices. These recommendations cover a wide range of security controls, including user authentication, access control, configuration settings, and more.
CIS has released more than 100 of these benchmarks, covering over 25 vendor product families. The technologies addressed by CIS Benchmarks can be generally classified into seven main categories.
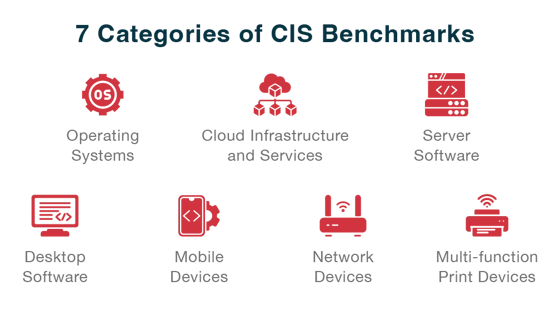
CIS benchmarks are designed for organizations of all sizes, but they are particularly beneficial if your company handles a lot of sensitive data, such as financial or healthcare data. The benchmarks provide you with a standardized approach to security, ensuring that your organization’s network is more resilient against potential threats.
So what’s the point? Why is CIS benchmarking so important?
Unlike some security frameworks that may seem daunting, CIS Benchmarks are designed to be accessible. You can start by reviewing the benchmarks relevant to your technology, giving them a try within your organization. If you need some clarity or simply don’t have the time to get it done on your own, professionals like Katalyst are here to help, providing guidance tailored to your specific needs and setup.
CIS benchmarks provide a common framework for securing various technologies. Whether you’re dealing with operating systems, network devices, or cloud environments, these benchmarks offer consistent guidelines that can be applied across different platforms.
This uniformity ensures that security measures are coherent and aligned, making management and monitoring more efficient.
Just as setting up 2FA can block 99.9% of automated cyber attacks, implementing CIS benchmarks can reduce your vulnerability substantially. By following the best practices outlined by CIS, organizations can significantly reduce the risk of data breaches and other security incidents. These guidelines are developed by cybersecurity experts and are based on real-world experiences.
One of the standout features of CIS benchmarks is that they are provided free of charge. Plus, these benchmarks are designed with real-world applications in mind, offering actionable guidance without requiring a complete network overhaul.
Whether you’re a small business or a large enterprise, these benchmarks can be integrated into your existing security strategy, enhancing protection without breaking the bank.
While all this information is readily available, the important thing is to actually implement it. Reading about best practices is one thing; putting them into action is what makes the difference. Here are some tips to get you started.
Implementing CIS Benchmarks is not just about flipping a switch. It can require significant setup, especially if you have multiple vendors in your setup. You may need a professional with a holistic view to come in and help.
While it might take work, the security enhancements are well worth the effort. Be mindful of overtooling however — this is a common pitfall that can rack up unnecessary expenses and complications you don’t want.
That said, embarking on the journey to secure your network using CIS Benchmarks doesn’t have to be an intimidating process. These benchmarks are designed with user-friendliness in mind, allowing organizations to take proactive steps towards enhancing their security.
Start by exploring the benchmarks and attempting to implement them within your system. Again, it’s better to do it correctly than to do it fast.
If at any point you feel overwhelmed or in need of specialized insight, Katalyst can help. The Katalyst team lives and breathes security, and can set up your security so you can go to sleep confident that your company’s data is protected.
To see what we’ve done for past clients, take a look at some case studies and project overviews.

Consulting Engineer

Discover three lesser-known, but equally threatening items posing risks to the health of your…

There are several reasons organizations engage in security assessment engagements. Learn what you…

What does the future look like for companies with young adults who’ve grown up with technology?…