
What is Katalyst’s Technology Business Canvas?
Find out about Katalyst’s Technology Business Canvas, a free service providing strategic IT and…
As leaders in any industry, we’re often forced to make timely decisions in the context of rapid change and new data coming in constantly. CIOs and CISOs in particular need to be able to respond intelligently to new situations, especially with the spike in cyber attacks in recent years.
In a high-stakes situation that moves quickly, the biggest cardinal sin is doing nothing — i.e. waiting until you have all the information before acting. It’s simply not realistic in a leadership position.
This makes it important to have mental models to rely on that have been tested and proven effective, whether in business, legal, or even military decision making.
If you’re unfamiliar with the term, a mental model is a kind of framework for representing and processing a problem, a way to simplify complex problems into something manageable.
A concept like “SWOT Analysis” is an instance of a mental model, as is the idea of a “bottleneck,” or “the law of diminishing returns.” No model is perfect, but they can be incredibly useful when used correctly.
A strong mental model can help make sure you’re iterating effectively in your decision making process, and doing it quickly.
Speed of decision making isn’t about being hasty, but knowing how to approach a problem effectively, and taking the initiative to do so when it’s identified.
Former US Secretary of Defense (and four-star general) Jim Mattis puts it like this:
“Speed is essential, whether in sports, business, or combat, because time is the least forgiving, least recoverable factor in any competitive situation. I learned to prize smooth execution by cohesive teams (those that could adapt swiftly to battlefield shocks) over deliberate, methodical, and synchronized efforts that I saw squelching subordinate initiative. In fact it was always subordinate initiative that got my lads out of the jams I got them into, my mistakes being my own.”
Charlie Munger — the Vice Chairman of Berkshire Hathaway, and Warren Buffet’s right-hand man — views mental models as mechanisms to enable the dismantling and solving of difficult problems.
Good judgment often depends on knowing which mental model to employ in a given situation: Munger says that leaders who don’t have multiple mental models at their disposal will risk failing disastrously. He suggests all business leaders be familiar with a “broad latticework of mental models” that can be selected from to allow new approaches to be applied to problems as needed.
One such mental model is the OODA Loop.
Now applied to a variety of fields, the OODA Loop was developed in the mid-20th century by the military strategist, US Air Force Colonel John Boyd. It was initially used to train individuals to make time-sensitive decisions rapidly when there may not be time to gather all the information.
The goal of the strategy was to execute the OODA Loop process more quickly than an opponent in order to infiltrate and disrupt the enemy’s decision cycle.
The OODA Loop stands for Observe, Orient, Decide, and Act. This mental model is an iterative process that is designed to help you make better decisions faster, especially when you’re dealing with complex, rapidly-changing situations, like cyber security threats.
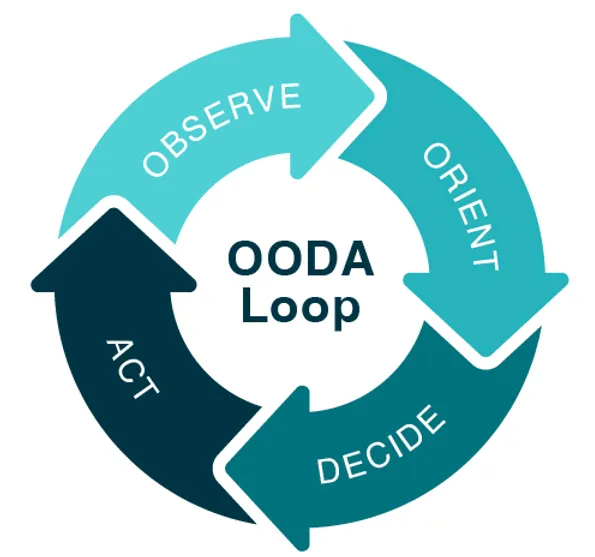
It works like this:
This is the data collection stage, or monitoring the security environment for potential threats. This could involve analyzing network traffic, checking for suspicious logins, or watching for unusual activity that could indicate a security breach.
In a network security incident, this might involve taking logs from your SOC/SIEM monitoring tools. Since these tools generate a lot of inconsequential data, it’s important to understand what’s relevant. That’s the next step.
This is where you process the data you’ve collected and try to make sense of it. You use your understanding of your organization’s systems and the broader cyber security landscape to interpret the data you’ve collected.
This stage might involve consulting with your team or outside experts, researching potential threats, or using tools to help identify patterns. For instance, AI and machine learning tools can filter out this superfluous information far more quickly than a human can.
Bear in mind that if you don’t have a baseline for what “normal” looks like, it’s harder to know when something is wrong, and harder to know what the correct decision is.
Once you’ve interpreted the data, you need to decide on a course of action. This might involve escalating the issue, implementing a security patch, or mobilizing your incident response team.
In the event of a cyber-attack, your strategy should cover all the necessary workflows to counter the attackers, rectify the inflicted damage, fix exploited vulnerabilities, and meticulously document the incident for future preparedness.
The solution you decide on will also need to allow for investigations into the origins, causes, and impact of the attack, which means resolving the issues without eliminating all the evidence. This could prove to be a critical asset for your future cybersecurity blueprint and may even be a legal necessity in certain scenarios.
Finally, you execute your decision. This might involve shutting down a compromised server, blocking a malicious IP address, or even alerting law enforcement. Either way, you need to reach this step quickly, and document your process.
Documentation is part of resetting the loop as you return to the observation stage, so you can have more established playbooks for similar situations in the future. Even if the plan fails, you have information to adjust your approach next time.
Once you’ve acted, you go back to the observation stage, collecting data on the impact of your actions and looking for new threats. The idea is to move through this loop faster than a potential attacker, disrupting their plans and staying one step ahead.
The OODA Loop can help you manage and respond to threats more effectively. It can also help you build a more resilient security posture by encouraging you to continuously observe your environment, adapt your strategies, and learn from your experiences.
Business leaders involved with cybersecurity need to be able to adapt and make informed decisions without delay. That’s why part of our work in providing managed security services is empowering clients to work through this loop more quickly: enhancing your ability to quickly understand a problem, make an informed decision, and take decisive action.
This involves breaking down the complex problems you have, filtering out what’s critical, and enabling you to make timely and well-informed decisions. In other words, you’re not just responding to threats, but staying one step ahead of them.
Learn more about how we help businesses like yours stay safe in today’s cyber environment.
Schedule a call to learn more about Katalyst’s tailored cybersecurity solutions designed to keep your organization and its data safe.

Find out about Katalyst’s Technology Business Canvas, a free service providing strategic IT and…

Explore the differences between SIEM, SOAR, and XDR. Learn their unique features, integration…

Learn the right questions to ask to ensure your company is optimized and ready for any…