Katalyst Network Group Blog
Resources and insights for technology and executive leaders

Are Your Teams’ Capabilities Getting Frumpy?
The shift to a programmatic world impacts our circles in a big way. Here are things you can focus…

Understanding your Applications
Are you in the process of incorporating cloud services? Learn what you should consider as part of…

Securing SD WAN
Learn the biggest impacts that SD-WAN has had on our market over the past year.

Katalyst Named to the 2020Tech Elite 250 by CRN®
Katalyst Named to the 2020Tech Elite 250 by CRN®

Assessing Self Assessment for Assessments
There are several reasons organizations engage in security assessment engagements. Learn what you…

Laying the Foundation for Cloud
With any cloud solution, proper security and network design are an integral part of the foundation….

The New Collaborative Culture
When it comes to learning new concepts or skills, there are “readers”, “seers” and “doers”. Get…

CyberPatriot Awards 2020
Reflecting on the CyberPatriot Awards Program and what young professionals can ask themselves as…
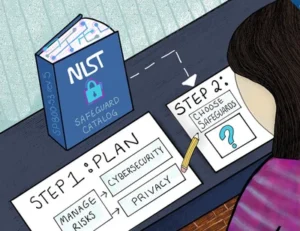
NIST Updates Its Core Catalog
The National Institute of Standards and Technology (NIST) provides key enhancements all…

